Cyber Safety Resources
- CyberTips
- How Did My Email Get Hacked
- Recognizing Phishing Attempts
- 10 types of Phishing Emails designed to trick you
- Example of a Deceptive Phishing Login Page
- Mobile Device Best Practices from the National Security Agency
- Checking and manually updating your web browsers

Tip #1 - You are a target to hackers
Don't ever think "It won't happen to me". We are all at risk and the stakes are high - to your personal and financial well-being.
- By following the tips below and remaining vigilant, you are doing your part to protect yourself and others.
Tip #2 - Keep software up to date
Installing software updates for your operating system and programs is critical. Always install the latest security updates for your devices:
- Turn on Automatic Updates for your operating system.
- Use web browsers such as Chrome or Firefox that receive frequent, automatic security updates.
- Make sure to keep browser plug-ins (Flash, Java, etc.) up to date.
- Utilize free or paid tools to find the other software on your computer that needs to be updated.
Tip #3 - Avoid Phishing scams - beware of suspicious emails and phone calls
Phishing scams are a constant threat - using various social engineering ploys, cyber criminals will attempt to trick you into divulging personal information such as your login ID and password, banking or credit card information.
- Phishing scams can be carried out by phone, text, or through social networking sites - but most commonly by email.
- Be suspicious of any official-looking email message or phone call that asks for personal or financial information.
Tip #4 - Practice good password management
We all have too many passwords to manage - and it's easy to take short-cuts, like reusing the same password. A password management program can help you to maintain strong unique passwords for all your accounts. These programs can generate strong passwords for you, enter credentials automatically, and remind you to update your passwords periodically.
There are several online password management services that offer free versions, and KeePass is a free application for Mac and Windows.
Here are some general password tips to keep in mind:
- Use long passwords - 20 characters or more is recommended.
- Use a strong mix of characters, and never use the same password for multiple sites.
- Don't share your passwords and don't write them down (especially not on a post-it attached to your monitor).
- Update your passwords periodically, at least once every 6 months (90 days is better).
Tip #5 - Be careful what you click
Avoid visiting unknown websites or downloading software from untrusted sources. These sites often host malware that will automatically, and often silently, compromise your computer.
If attachments or links in email are unexpected or suspicious for any reason, don't click on it.
Tip #6 - Never leave devices unattended
The physical security of your devices is just as important as their technical security.
- If you need to leave your laptop, phone, or tablet for any length of time - lock it up so no one else can use it.
- If you keep sensitive information on a flash drive or external hard drive, make sure to keep these locked as well.
- For desktop computers, lock your screen.
Tip #7 - Protect sensitive data
Be aware of sensitive data that you come into contact with, and associated restrictions
In general:
- Keep sensitive data (e.g., SSN's, credit card information, student records, health information, etc.) off your workstation, laptop, or mobile devices.
- Securely remove sensitive data files from your system when they are no longer needed.
- Always use encryption when storing or transmitting sensitive data.
Tip #8 - Use mobile devices safely
Considering how much we rely on our mobile devices, and how susceptible they are to attack, you'll want to make sure you are protected:
- Lock your device with a PIN or password - and never leave it unprotected in public.
- Only install apps from trusted sources.
- Keep your device's operating system updated.
- Don't click on links or attachments from unsolicited emails or texts.
- Avoid transmitting or storing personal information on the device.
- Most handheld devices are capable of employing data encryption - consult your device's documentation for available options.
- Use Apple's Find my iPhone or the Android Device Manager tools to help prevent loss or theft.
- Backup your data.
Tip #9 - Install anti-virus protection
Only install an anti-virus program from a known and trusted source. Keep virus definitions, engines and software up to date to ensure your anti-virus program remains effective.
Tip #10 - Back up your data
Back up on a regular basis - if you are a victim of a security incident, the only guaranteed way to repair your computer is to erase and re-install the system.
Here are some additional tips to help keep you safe and secure online:
- Use a firewall - Mac and Windows have basic desktop firewalls as part of their operating system that can help protect your computer from external attacks.
- Use public wireless hot-spots wisely - follow these tips for staying safe.
- Be conscientious of what you plug in to your computer (flash drives and even smart phones can contain malware).
- Be careful of what you share on social networking sites.
- Monitor your accounts for suspicious activity.
- Bank or shop online only on trusted devices and networks - and logout of these sites when you've completed your transactions.
- Review the FBI’s SCAMS and SAFETY tips
Here are some of the most common causes below:
- You fell for a phishing scam that asked you to “confirm” your password. These types of scam emails can be convincing. But you should never respond to any unexpected message that asks you to verify your password, account numbers, addresses, or any other information of this kind.
- You didn’t log out of your account after using a public PC or device. Aside from getting into the habit of logging out each time you use a shared device, it’s wise to avoid using public PCs altogether (like the ones you find at internet cafes and libraries, and AIRPORTS). There’s really no way to know whether these machines are infected with malware or have keylogging spyware installed on them, making them a big risk.
- You used a weak, easy-to-guess password or have been using the same password across multiple sites. Make sure your passwords are both long and unique for all the various sites and services that you use. A good rule of thumb: make them at least 16 characters. To make them easy to remember, base them on a complex sentence, with the first letter of each word serving as a character in your password.
- You didn’t use up-to-date security software on your PC or PHONE. Without adequate protection, your PC or PHONE can become infected with malware designed to steal your passwords – sneaking through in the form of dodgy downloads and suspicious email attachments.
- You used an unsecure Wi-Fi network where hackers were able to eavesdrop on your data and intercept your passwords. To avoid this, you should only ever connect to reputable networks that you trust, and which are password protected.
- Your email address was harvested by spammers. This happens when you list your email address publicly online — in places like forums, online ads, blogs, etc. Just don’t do it. For the great majority of us, there is no reason to publish an email address on the internet.

Phishing Attempts Explained
- Email scams and phishing messages are types of electronic fraud that request recipients to disclose information or perform other potentially harmful actions on behalf of the sender.
- These types of emails appear to come from reliable sources like credit card company or your banking institution, and often contain urgent requests that require the recipient to provide sensitive information―passwords, account numbers, etc.―by either replying to the email directly or by entering this information on a bogus website.
- While ITD makes a valiant effort to prevent email scams from reaching you and does block a lot of malicious messages from being distributed to the City e-mail system. Sometimes, malicious and junk email slips through this security net.
Best Practices
- The best defense against malicious email attempts is an educated user. When you receive any email requesting personally identifiable information, follow these best practices to protect yourself and the City:
Never reply to unsolicited e-mails
- Messages that asks for your personal information including requests for NetID passwords, Social Security Numbers, or requests for credit card information should not be trusted. Most institutions (Northwestern, your bank or credit card company, etc.) will not email you requesting this type of information.
Never reply to unsolicited e-mails (We are saying it again!!)
- Messages that asks for your personal information including requests for NetID passwords, Social Security Numbers, or requests for credit card information should not be trusted. Most institutions (Northwestern, your bank or credit card company, etc.) will not email you requesting this type of information.
Do not click on links directly from emails
- Open a new browser and find the supposed institution’s website yourself through a search engine or URL bar.
Be on the lookout for suspicious emails
- Messages with suspicious, misspelled, or awkward language, or that reference non-existent City departments like "City Webmail Support" or the "Webmail Messaging Center" are examples of scam emails. Pay attention to unusual greetings or signatures from messages purporting to be from your contacts.
Delete messages that are confirmed to be phishing
- If you confirm or recognize a message to be a phishing attempt, delete them from your "Inbox" and your "Deleted Items" folder to avoid accidentally accessing the Web sites within the bogus email.
Do not send your personal information
- Never send personally identifiable information, such as passwords, credit card account numbers, and Social Security Numbers, through email.
Update software often
- Regularly update and use antivirus and anti-spyware software, and your firewall. Be sure your applications and anti-virus software is the most current.
Always be cautious
- Remember to always be cautious about opening any attachments or downloading any files from emails you receive, regardless of who sent them.
Other Types of Phishing
- Phishing isn’t just for email anymore! Be aware of attacks through phone calls, texts, or other online messaging applications. Make sure you're on the lookout for these variants on the traditional, mass emailed phishing attack:
Spear Phishing
- This kind of attack involves often very well-crafted messages that come from what looks like a trusted VIP source, often in a hurry, targeting those who can conduct financial transactions on behalf of your organization (sometimes called "whaling").
SMiShing
- Literally, phishing attacks via SMS, these scams attempt to trick users into supplying content or clicking on links in SMS messages on their mobile devices. Flaws in how caller ID and phone number verification work make this an increasingly popular attack that is hard to stop.
Vishing
- Voice phishing, these are calls from attackers claiming to be government agencies such as the IRS, software vendors like Microsoft, or services offering to help with benefits or credit card rates. Attackers will often appear to be calling from a local number close to yours. As with SMiShing, flaws in how caller ID and phone number verification work make this a dangerous attack vector.
Social Media Phishing
- Attackers are increasingly turning to social media for their phishing attacks. Many people are suspicious of blatant phishing attacks on social media, such as a stranger messaging you through a private message on social media with a link to click. But other schemes are harder to spot. Attackers often take over accounts and then target their friends with phishing attacks. Other schemes include social media quizzes that get users to enter information that can then be used for social engineering accounts. Threat actors also create clone accounts of real companies to get people to click on malicious links thinking they are trustworthy.

Typically, phishers send legitimate looking emails that appear as though they originated from reputable companies that many people do business with like BestBuy, Amazon, Federal Express, DHL, and PayPal.
✓ The emails often ask customers to confirm information or to go to the business site by clicking on a provided link, and often include a statement of impending consequences if you fail to act.
Here are 10 types of phishing e-mails designed to trick you:
1. The Government Maneuver
This type of email looks like it originated from a federal body, such as the FBI, and tries to scare you into providing your information. Common messages include, ‘Your insurance has been denied because of incomplete information. Click here to provide your information.’ Or, ‘Because you illegally downloaded files, your Internet access will be revoked until you enter the requested information in the form below.’
2. The Friend Tactic
If an unknown individual claims to know you in an email, you are probably not suffering from amnesia. More than likely, it is an attempt to get you to wire him/her money. A variation on this theme is that one of your known friends is in a foreign country and needs your help. Before you send your ‘friend’ money, give them a call to verify. Your true friend’s email contact list was probably hijacked.
3. The Billing Problem
This phishing tactic is tricky because it appears quite legitimate. This email states that an item you purchased online cannot be shipped to you because the credit card was expired (or billing address wasn’t correct, etc.). If you click on the provided link, it takes you to a spoofed website and asks for updated payment/shipping information, etc.
4. The Expiration Date
This type of email falsely explains that your account with [company name] is about to expire, and you must sign in as soon as possible to avoid losing all your data. Conveniently enough, there is a link in the email, which again takes you to a spoofed login page.
5. The Virus or Compromised Account Scare
These types of email state that your computer has been infected or that one of your accounts has been breached. In order to avoid losing your money or data or infecting your computer the email instructs you to follow a link to download the attachment.
6. The Contest Winner
Don’t get too excited when you receive emails that claim you’ve won something, or received an inheritance from a relative you've never heard of. 99.9% of the time, these are absolutely bogus. To claim your prize, the email requires you click a link and enter your info for prize shipment.
7. The Friendly Bank
Your bank may offer account notifications when certain amounts are withdrawn from your accounts. This ploy tricks you with a fake account notification stating that an amount has been withdrawn from your account that exceeds your notification limit. If you have any questions about this withdrawal (which you probably would), it gives you a convenient link that leads to a web form asking for your bank account number “for verification purposes.” Instead of clicking on the link, give your bank a call. They may want to take action on the malicious email.
8. The Victim
Being wrongly accused of something doesn’t feel good. This type of phishing email acts as an angry customer whom supposedly sent you money in return for a shipped product. The email concludes with the threat that they will inform the authorities if they don’t hear from you.
9. The Tax Communication
Practically everyone has annual taxes to submit. That’s why this phishing attempt is so popular. The message states that you are either eligible to receive a tax refund, or you have been selected to be audited. It then requests that you submit a tax refund request or tax form.
10. The Checkup
This is one of the more unassuming phishing email attempts. It claims [company name] is conducting a routine security procedure and requests you verify your account by providing information. This scam is especially effective if you happen to be a customer of the named business.
* The images dispayed on this page are from the pixabay website which provides stunning free images and royalty free stock.
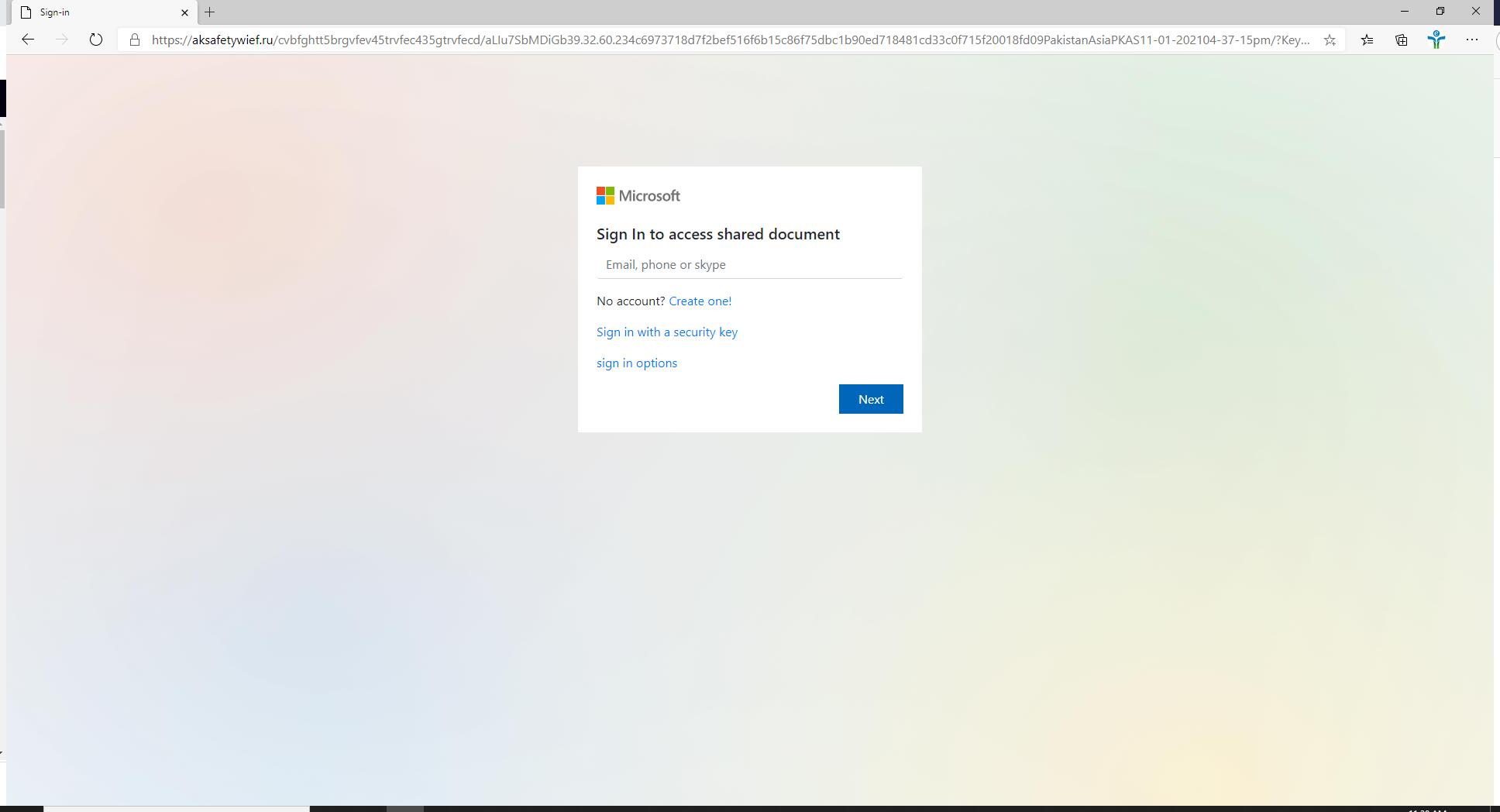
Below is an example of a page trying to steal a persons Office 365 login credentials. Notice it looks the same or very close to the real Microsoft page. Pay close attention to the information in the URL line. In it, you can see that the location isn't even close to Microsoft's authentication site. This page is from an Excel spreadsheet sent as an attachment by a Spammer.
All modern day browsers automatically check for updates upon launch by default.
- Chrome
- Click on the three dots in the top right.
- Select Help and then About Google Chrome, which will automatically check for updates and then apply it if one is available.
- Click on the three dots in the top right.
- Firefox
- Click on the hamburger (3 lines) in the top right.
- Select Help and then About Firefox, which will automatically check for updates and then apply it if one is available.
- Click on the hamburger (3 lines) in the top right.
- Edge
- Click on the 3 dots in the top right.
- Select Help and Feedback and then About Microsoft Edge, which will automatically check for updates and then apply it if one is available.
- Click on the 3 dots in the top right.
- Safari
- Safari will update with the MacOS update process like all applications do on the Mac.
- Brave
- Click on the hamburger (3 lines) in the top right.
- Select About Brave, which will automatically check for updates and then apply it if one is available.
- Click on the hamburger (3 lines) in the top right.
* The images dispayed on this page are from the pixabay website which provides stunning free images and royalty free stock.